
Program to be available on Web free in three weeks

Managing Editor
Some 2,975 AIA members* at 245 sites took part in "Security by Design: Insights and Best Practices," a 90-minute virtual seminar the AIA presented live November 5. The program, which the national component offered free of charge to AIA components and firms, was made possible through the generous support of Autodesk.
The five presenters—four architects and a security expert—offered to the audience case studies, guidelines, and rules of thumb for addressing security concerns in new construction and existing buildings. Autodesk's AEC Market Group Vice President Phillip G. Bernstein, FAIA, and AIA Executive Vice President/CEO Norman L. Koonce, FAIA, welcomed the seminar participants across the country. "The strength of our profession lies in the willingness of architects to share best practices," Koonce said. He envisions the security program to be the beginning of a new way for AIA members to share information.
Getting a handle
on security design
How to think about security: Robert Craig, CPP, manager, security division,
Rolf Jensen & Associates, Fairfax, Va. kicked off the program with
an overview describing the three main issues affecting building design:
terrorism, the urban environment, and American business. He pointed out
that in the U.S., almost all terrorist attacks have been against businesses,
and shared the "motives, means, and methods" of terrorism, including
the fact that 26 nations now have the means to launch chemical and biological
attacks. Craig also took the group through the roles of security with
the built environment: first deterrence (avoid intrusion in the first
place), then detection (minimize it), then delay (mitigate it).
 Work
with the site first: Robert Barr, AIA, senior principal, Hellmuth,
Obata & Kassabaum, Washington, D.C., covered the steps of his company's
approach to thinking about security, a process that parallels the steps
of the early design process:
Work
with the site first: Robert Barr, AIA, senior principal, Hellmuth,
Obata & Kassabaum, Washington, D.C., covered the steps of his company's
approach to thinking about security, a process that parallels the steps
of the early design process:
• Threat assessment
• Security audit
• Vulnerability assessment
• Facility categorization
• Objectives definition
• Design preparation.
Barr also compared selection of an urban site (the security for which is more often dictated by existing conditions) and a suburban site (which allows more creativity with site conditions for creating secure environments). He walked the audience through a case study for the design of the U.S. Embassy in Croatia, which employs highly controlled access of people and goods—even to the roof—and a blast-resistant skin. Barr emphasized that "a secure building does not have to look like a small-windowed hotel" or fortress.
Security elements can be attractive: One of the most celebrated secure buildings, the Oklahoma City Federal Building, which replaces the Murrah Federal Building toppled by a terrorist bomb in 1995, was presented by its designer, Carol Ross Barney, FAIA, principal, Ross, Barney & Jankowski Inc., Chicago. Ross Barney walked participants through the $31 million structure, which, with 180,000 square feet, is about the size of its predecessor. On the edge of the Oklahoma City central business district and kitty-corner to the former site of the Murrah Building, the project is on track to open in mid-2003.
 The
new federal office building employs a 50-foot standoff distance from the
street for blast protection, and is surrounded by bollards for vehicular
access control. The gentle cadence of the repetitive bollards, plus a
large courtyard fountain that "creates a modest type of moat"
prove that "security elements can be attractive," Ross Barney
said. The design employs another security rule of thumb: Where you can't
control the threat, keep that piece outside of the building, as demonstrated
by the federal building's pulled-out stair towers.
The
new federal office building employs a 50-foot standoff distance from the
street for blast protection, and is surrounded by bollards for vehicular
access control. The gentle cadence of the repetitive bollards, plus a
large courtyard fountain that "creates a modest type of moat"
prove that "security elements can be attractive," Ross Barney
said. The design employs another security rule of thumb: Where you can't
control the threat, keep that piece outside of the building, as demonstrated
by the federal building's pulled-out stair towers.
Designs and devices: Denis Goeser, AIA, project manager, Leo A. Daly, Omaha, presented a range of materials and strategies to cope with three levels of protection to a building: low (collapse is prevented), medium (the structure remains salvageable), and high (the building sustains minor damage). External devices ranged from intrusion detection systems (motion, heat, sound, and electronic) to predetonation screens, and internal devices ranged from blast curtains to service tunnel restrictions.
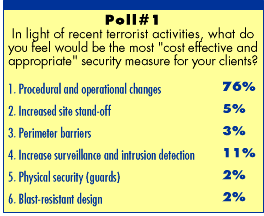 Among
the number of tips Goeser presented through many case studies, perhaps
most interesting at the moment were strategies to deter chemical and biological
threats, including filtration (perhaps even in-line irradiation), airlocks
at entries, and protection of air intakes. The firm's new Italian Chancery
Building in Washington, D.C., even contains a "man trap" that
captures intruders and keeps them until the authorities arrive.
Among
the number of tips Goeser presented through many case studies, perhaps
most interesting at the moment were strategies to deter chemical and biological
threats, including filtration (perhaps even in-line irradiation), airlocks
at entries, and protection of air intakes. The firm's new Italian Chancery
Building in Washington, D.C., even contains a "man trap" that
captures intruders and keeps them until the authorities arrive.
Security flow: "It would be irresponsible to waste the client's money on ineffective security measures," declared Michael Patrick, AIA, director, architectural design, Leo A. Daly, Atlanta, as he explained the cost vs. protection analysis in deciding which security measures to put into place. Using the firm's work in Washington, D.C.'s Reagan National Airport as an example, Patrick also explained the concept of "secure flow" for airports, which entails striving for both improved security and smoother flow throughout the facility. The notion of secure flow has been accelerated by the September 11 terrorist attacks, Patrick said. For instance, 100-percent x-raying of checked baggage originally was supposed to be in place by 2009; since the attacks, that schedule has been moved forward to 2004.
Patrick also presented a fascinating array of airport security devices, including biometric recognition devices that can pick out and track a face in a crowd, to radio-frequency luggage tags to seal bags and track the location of any piece of luggage (one major airline already uses this system).
 A
word about the format
A
word about the format
Taking part in a virtual seminar—especially in a wide-screen presentation—is
difficult to describe. It offers a highly experiential way to learn. It's
fast-paced, fun, and a good way to concentrate your attention on design
and technical material. If you haven't tried one, you might want to put
it on your list of "new things to do in '02."
The format seems tailor-made for architects—both on the giving and receiving end. It enables speakers to present a wide range of visual presentation—drawings, photos, and maps. They can highlight and draw on the images to make their points as they are talking. They can jump in and out of the conversation, helping each other out or sparking debate. The audience also gets its chance to take part. Polls are interspersed throughout the talks, allowing mini-breaks in listening. Results are compiled instantly and the votes show up on the screen as they are compiled electronically. The audience also can ask questions live via telephone or email in their queries.
The programs are timed out beforehand and adhere to a preset schedule--in other words, they keep moving right along. The program is introduced and shepherded by a moderator (in this seminar it was Ted Tatara), which keeps the keeps the presentation going.
If you missed it,
sign up now for the Web presentation
If you did miss the November 5 presentation, you can register
in advance to view the taped seminar free of charge, courtesy of KRM
Information Services, Inc. By registering in advance, registrants will
be notified automatically when the archived program is available. Anyone
may access the archived program, including those who took in live the
event.
Copyright 2001 The American Institute of Architects. All rights reserved.
![]()
|
*How the audience size was
estimated: Click here for participants' comments. HOK Senior Principal Robert Barr used the firm's design for the
U.S. Embassy in Croatia as a case study for a suburban-type security-conscious
building. The Oklahoma City Federal Building by Ross, Barney & Jankowski
Inc. employs many site and building elements, such as a courtyard
fountain that enhance both security and attractiveness of the site. |
|